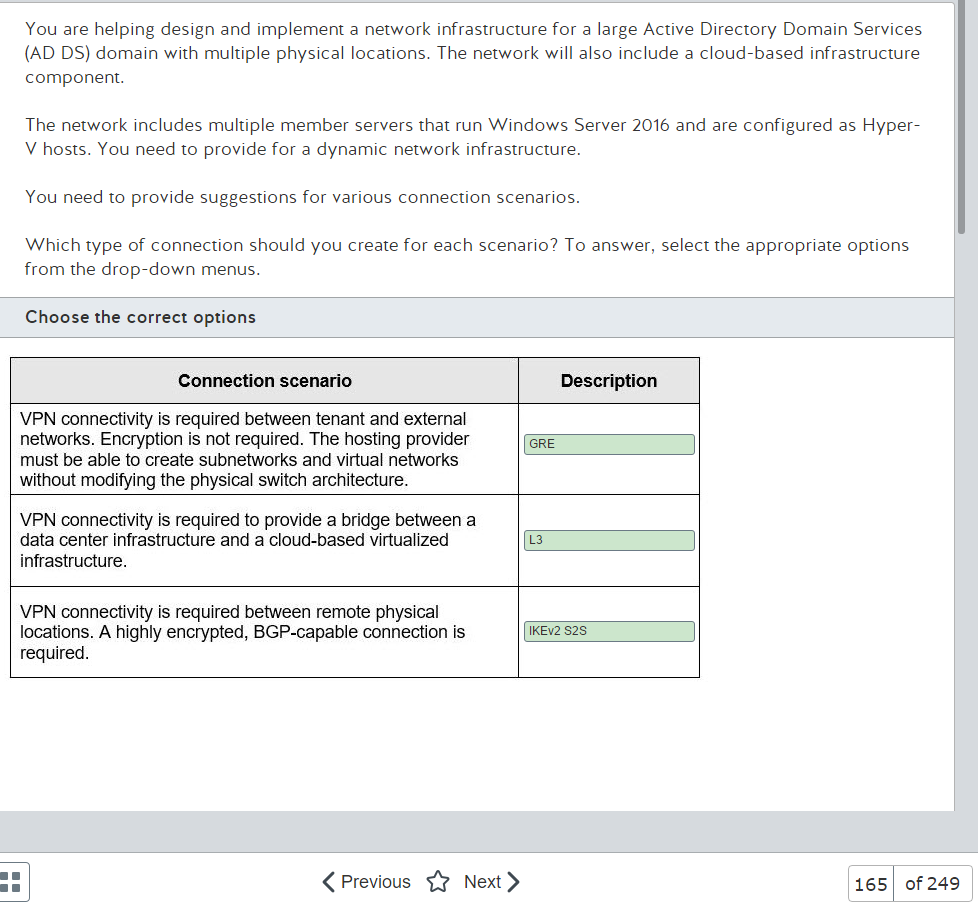
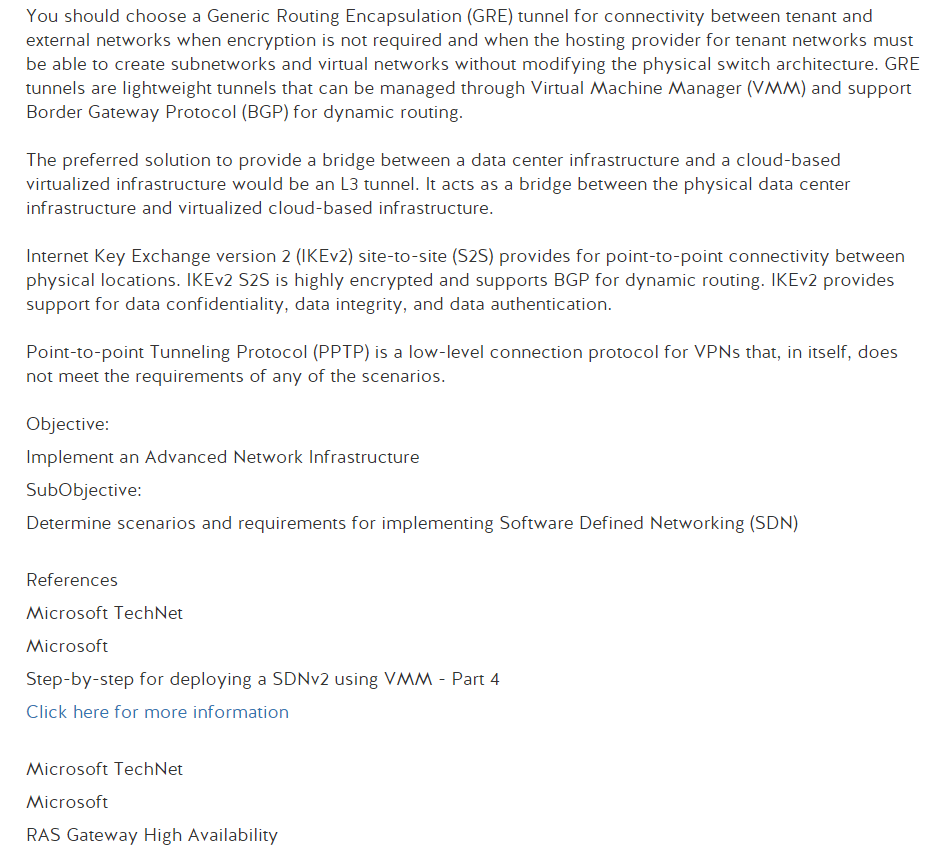
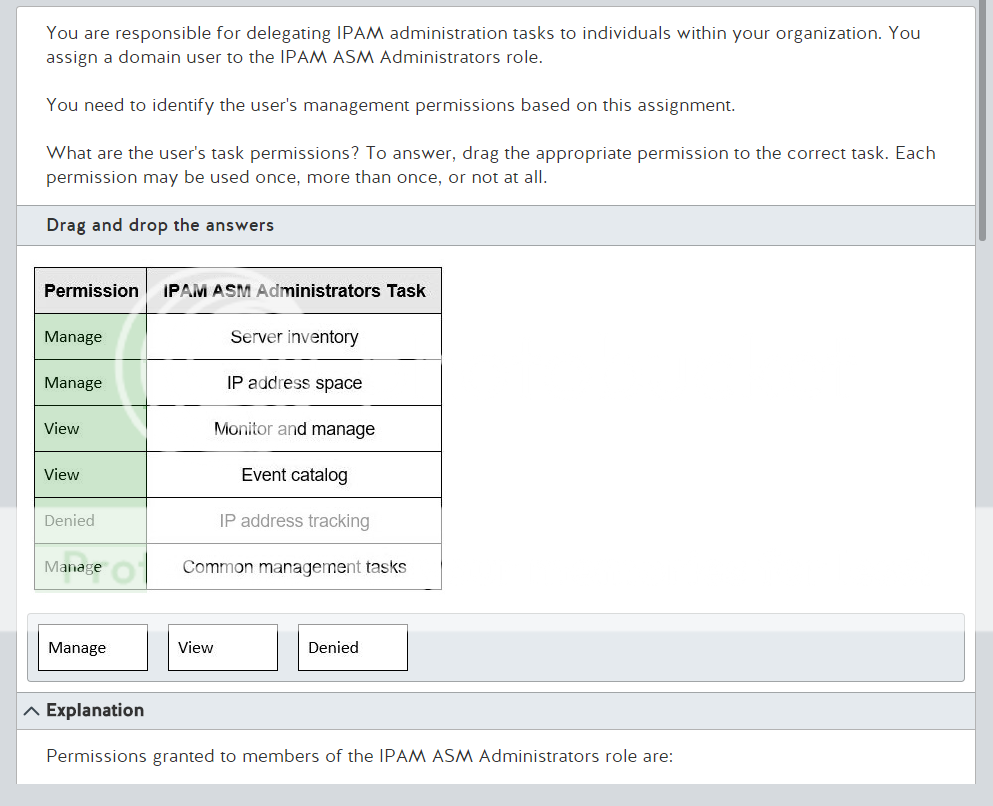
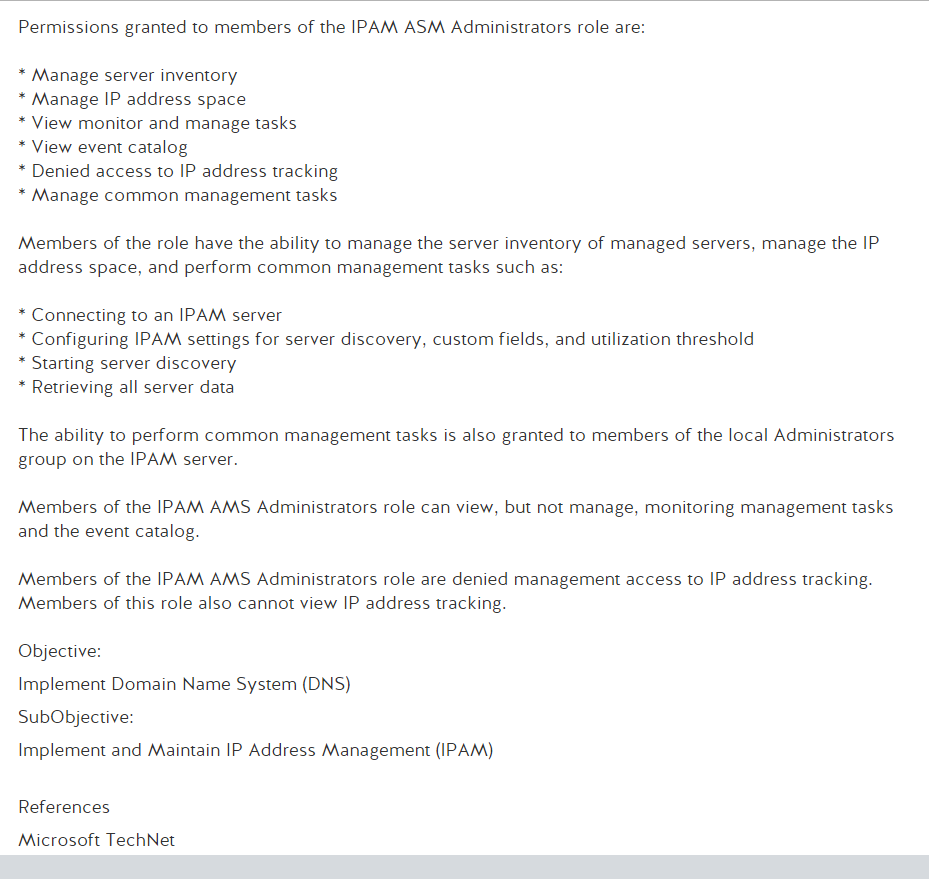
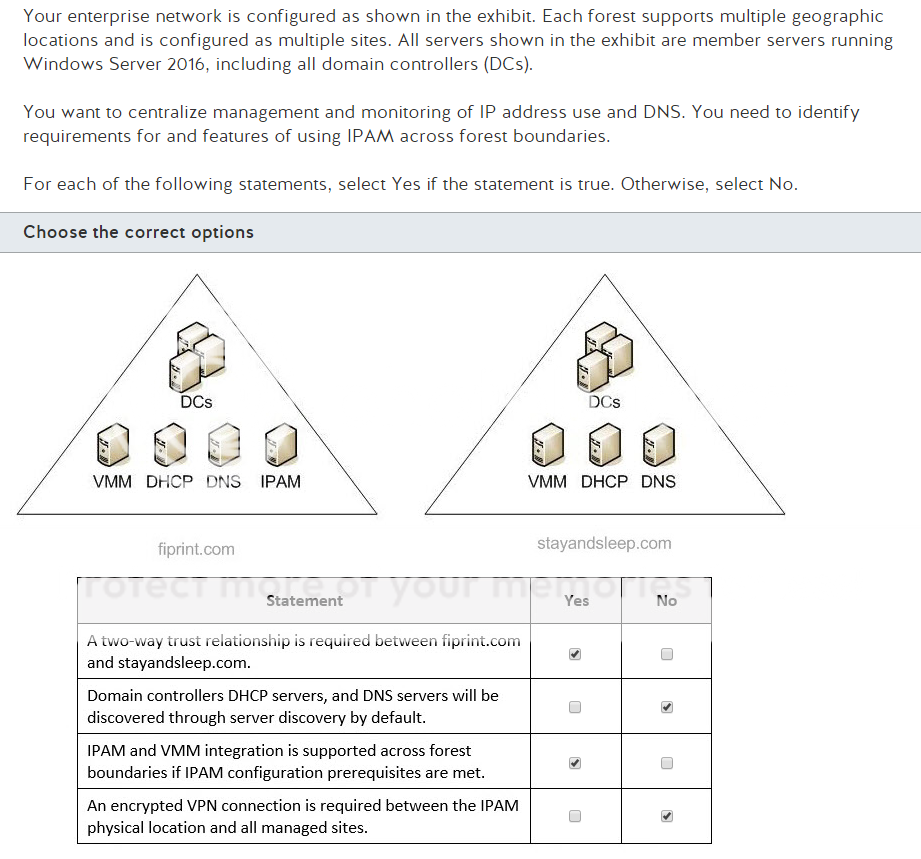
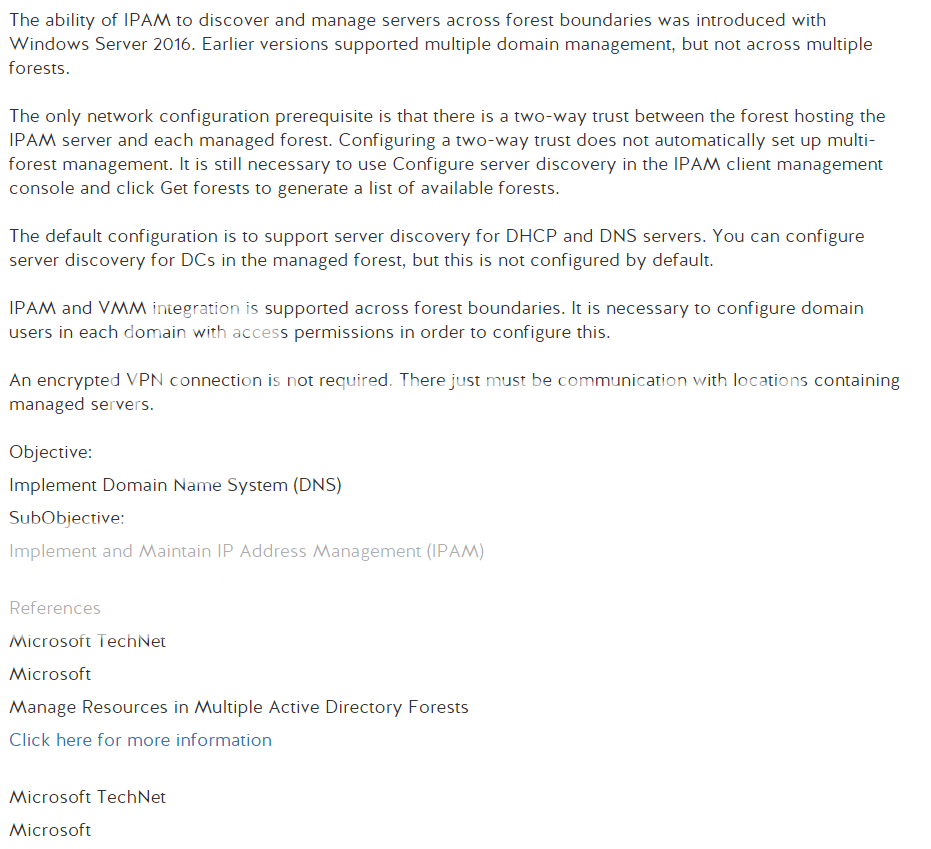
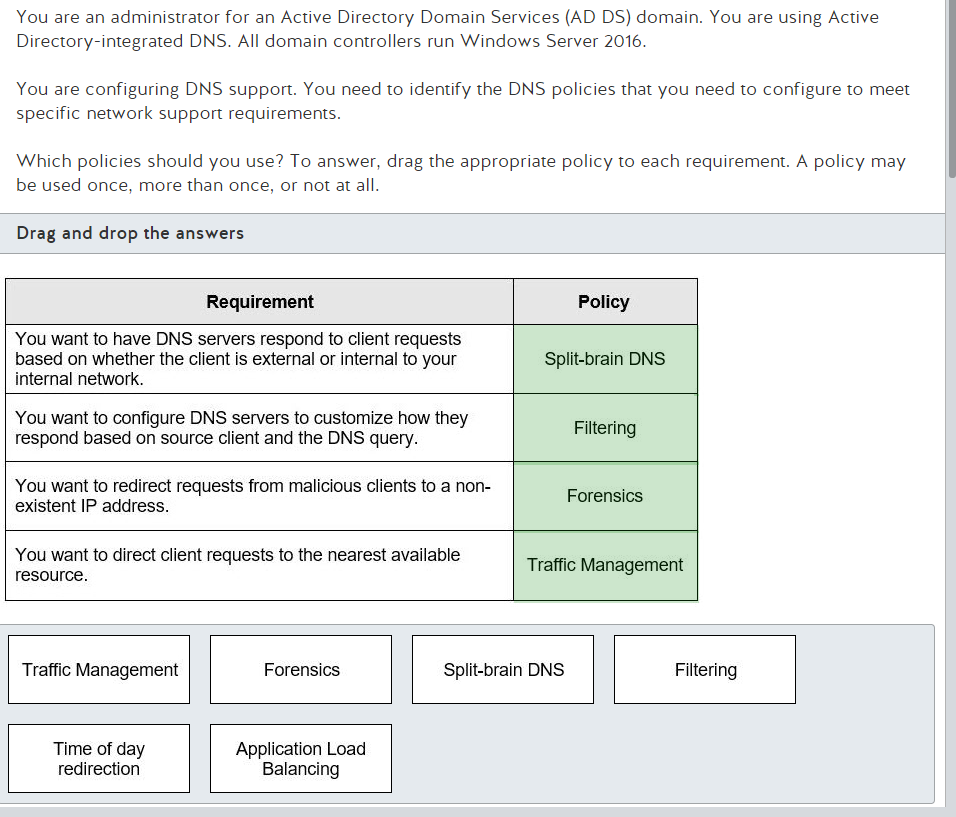
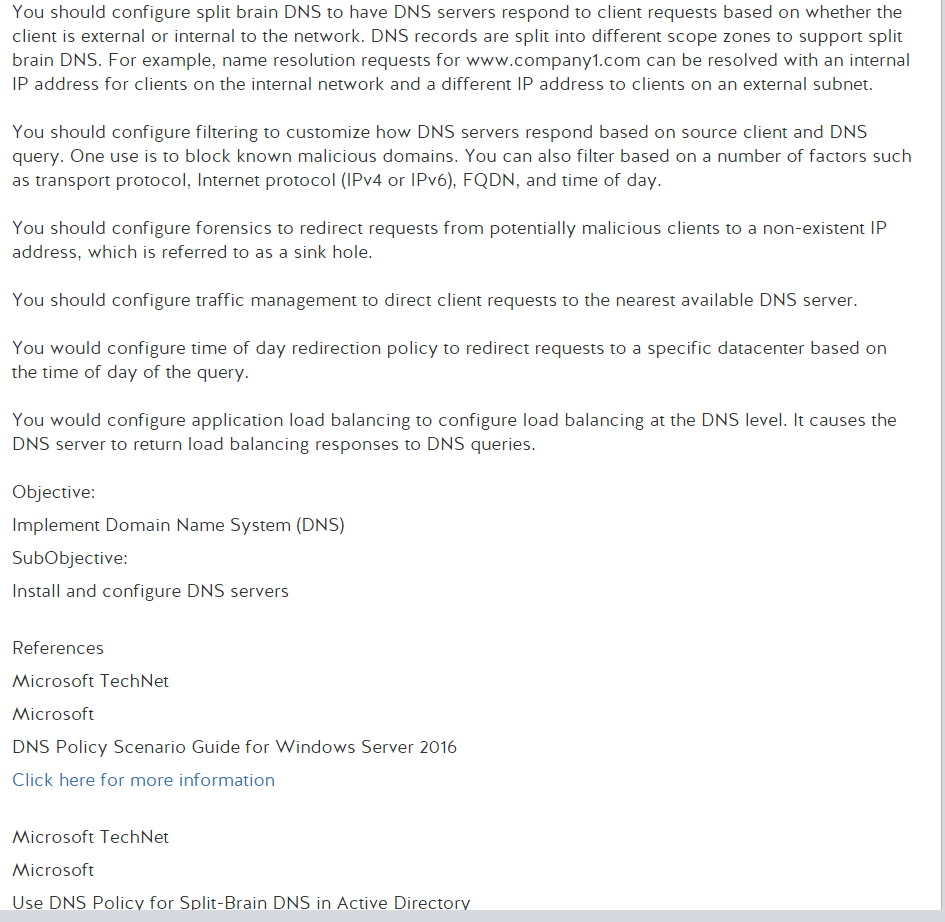
Well its Monday, time to start something new. I’m ready to get into Network+ and maybe go through to PenTest+ over the course of the next year. Regardless it would be great to get Network+ done by year end. Which seems doable but I could be wrong. Anyway, lets get into that thing that I use this blog for where I post a slide and then break it down until I figure out whats going on because memorizing answers does not do it for me.
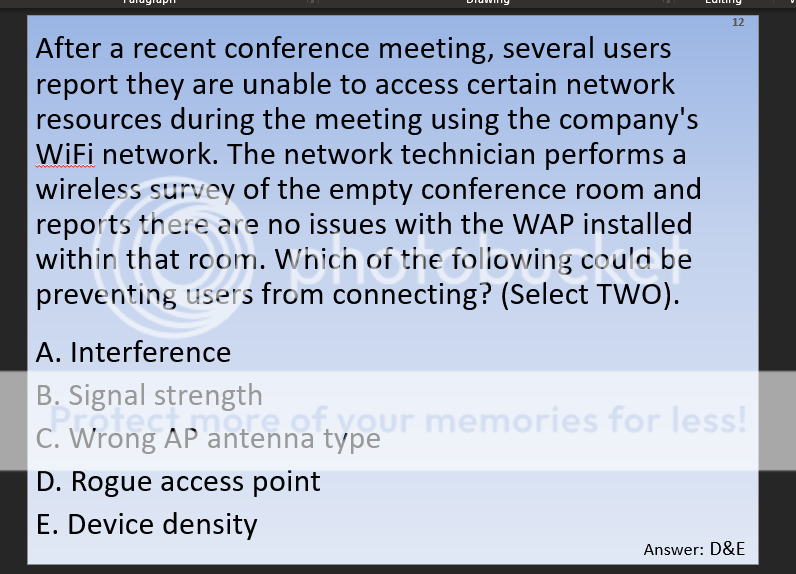
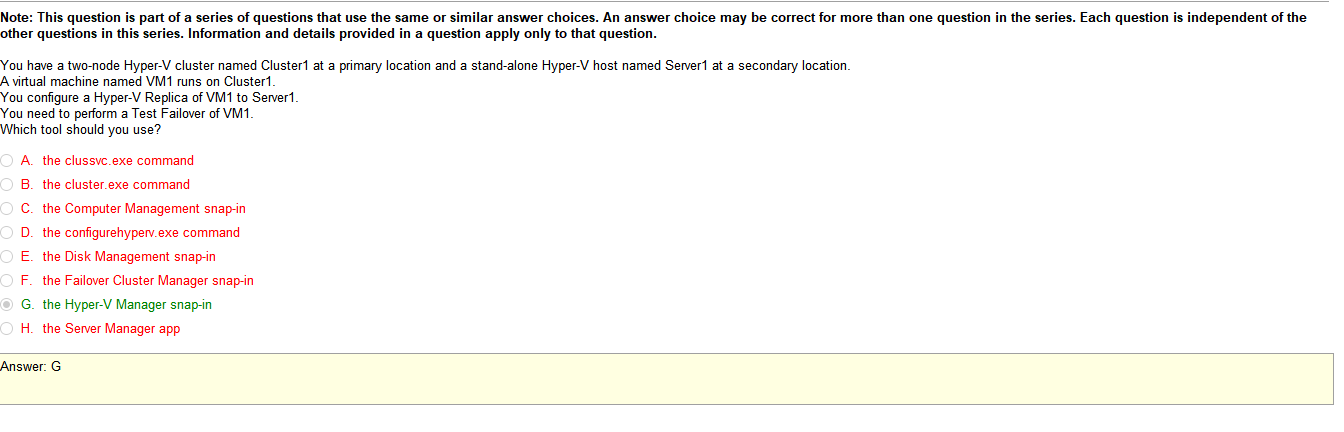
The longer I look at this the more I’m not sure why I added it other than I didn’t really know what they meant by device density. Like are they using old laptops or something? I mean it would be a safe assumption I suppose. The other thing I hate about comptia stuff is that they use language that I’m assuming you cant pull from the web to study for. Like maybe this stuff is in a book. Did a quick search and it mentions the concept as a bullet point then gives no further info.
Ok so this does exist: What is network density
Ok jeeze, that does make sense. It doesn’t specifically say timeout errors connecting to resources but that makes sense. A rouge access point would also provide for this as its possible to have internet access and no access to internet resources, clearly.
I dont really know what any of this stuff is so I’m going to have to start by looking up each of these terms, just to be through.
-
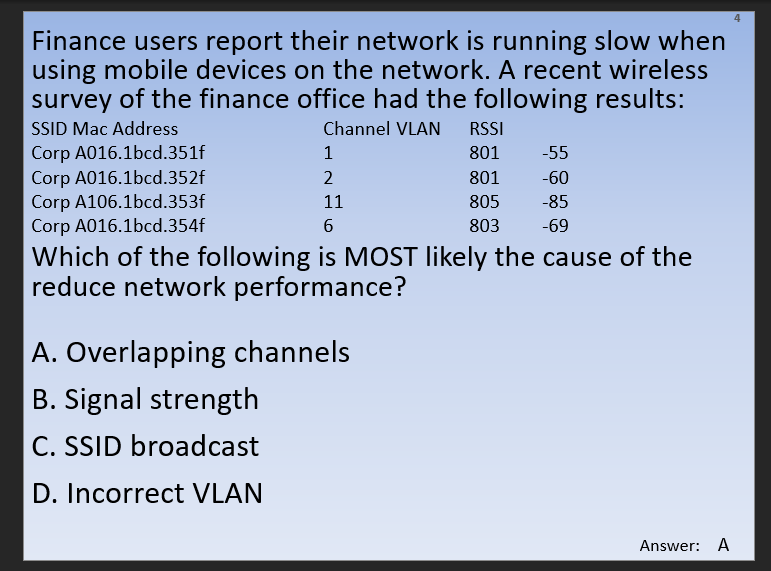
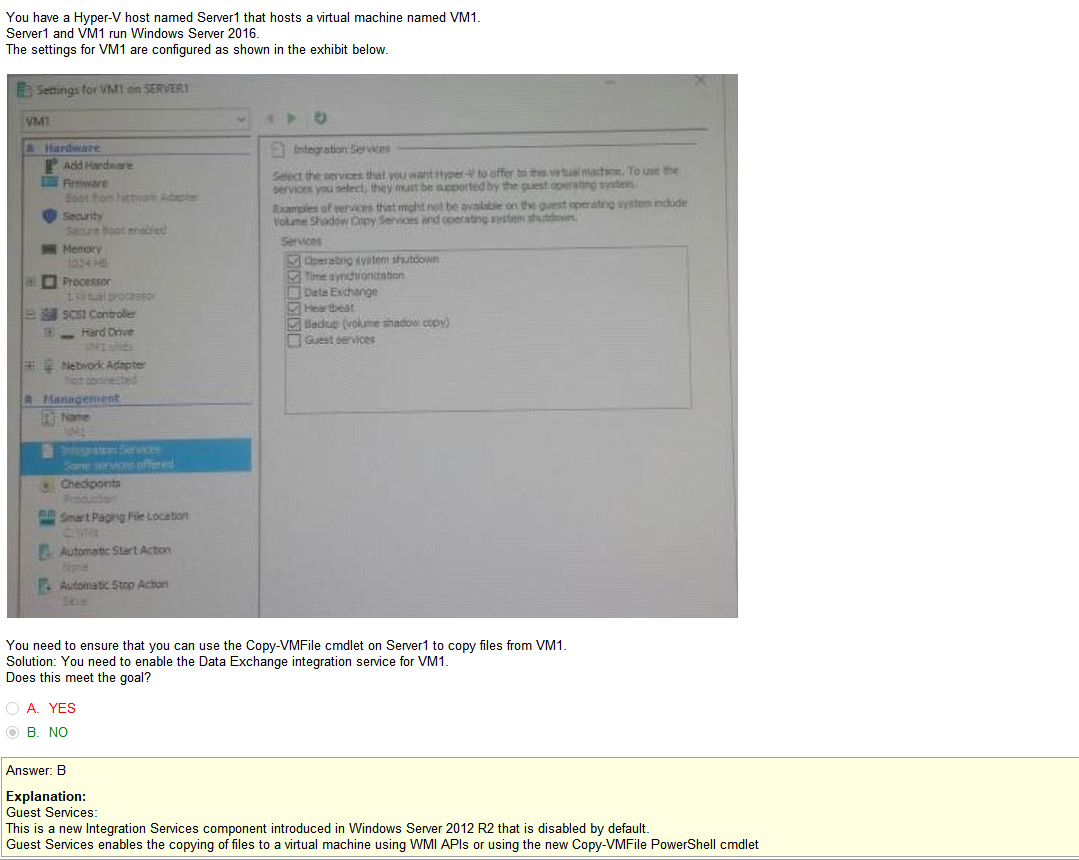
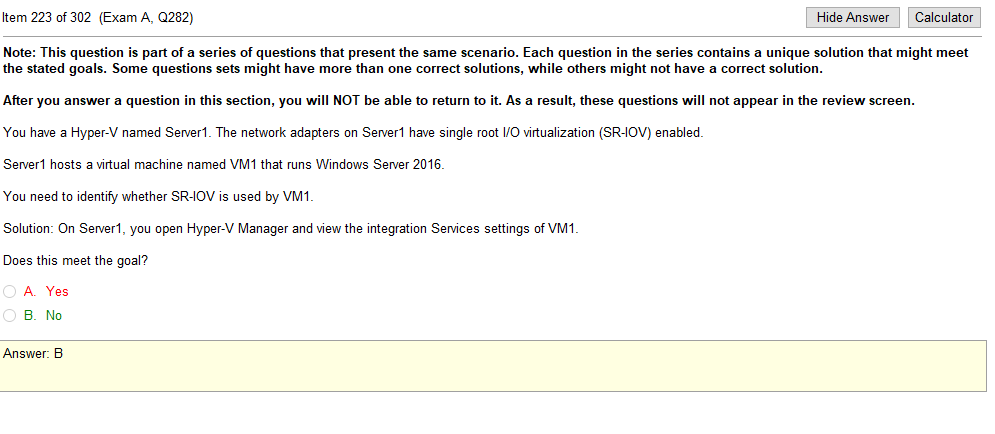
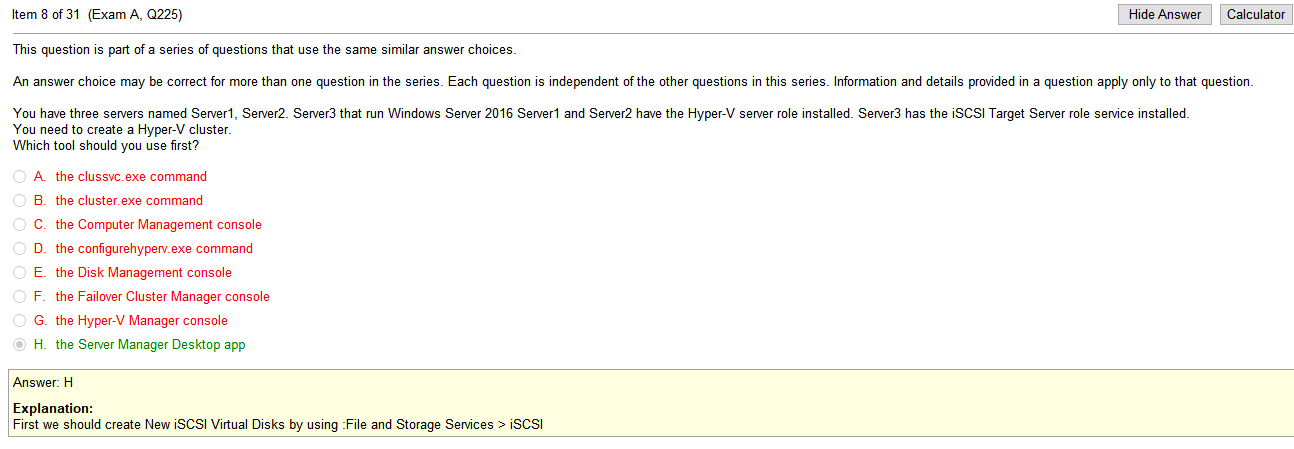
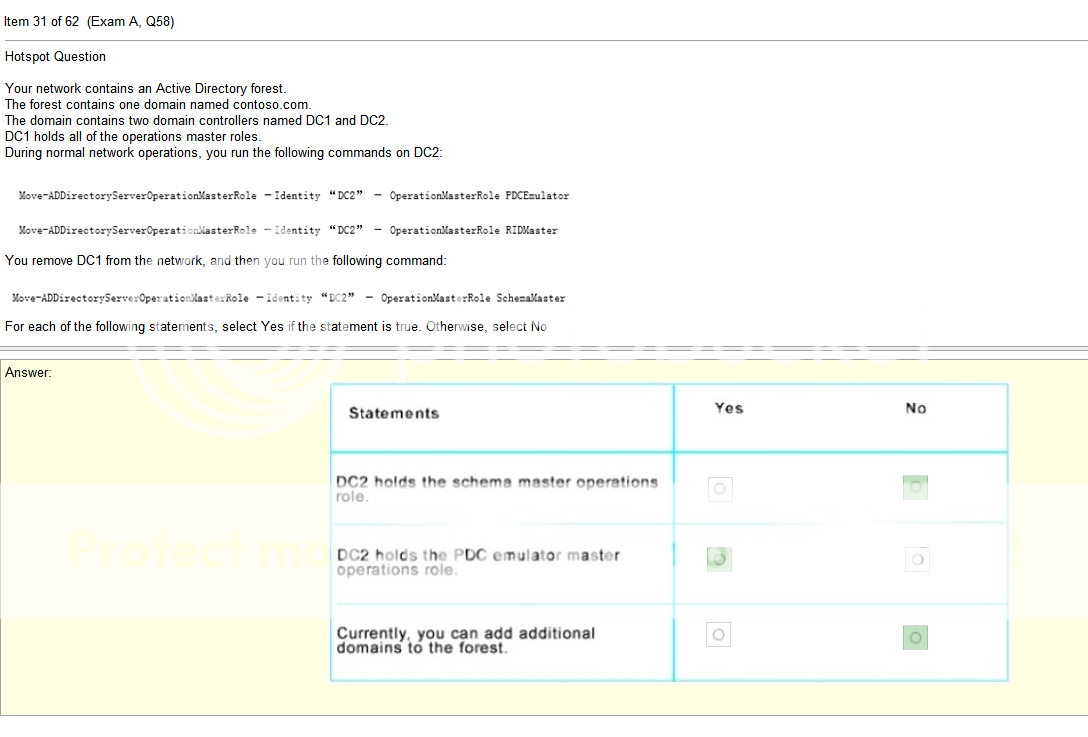
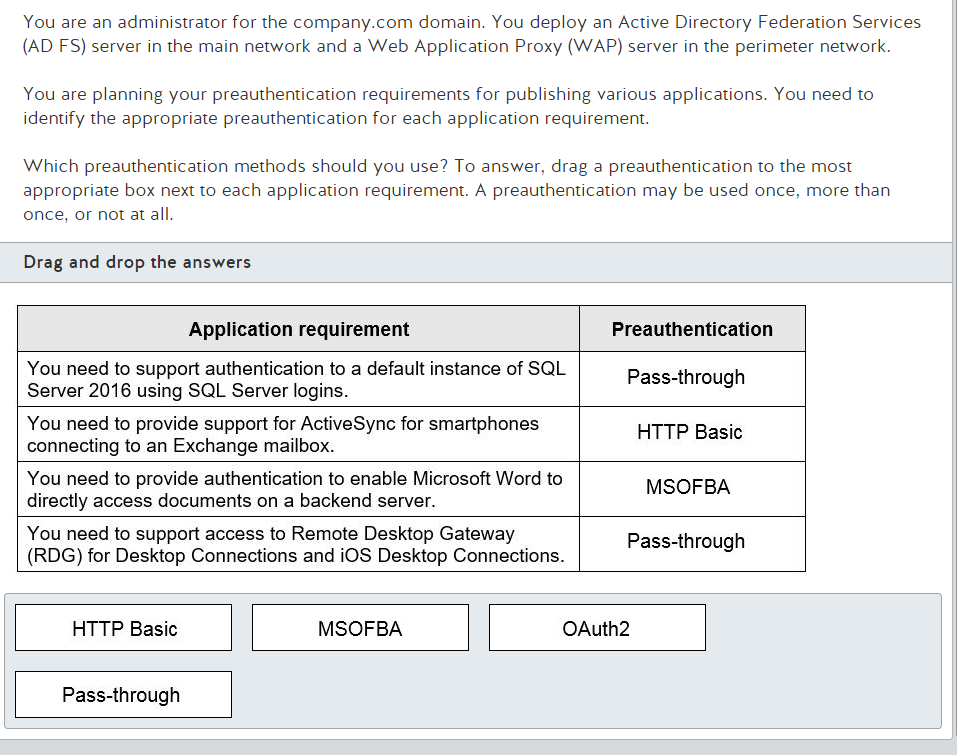
Stuff in question
- Rssi- RSSI stands for Received Signal Strength Indicator. It is an estimated measure of power level that a RF client device is receiving from an access point or router. At larger distances, the signal gets weaker and the wireless data rates get slower, leading to a lower overall data throughput.
- channel vlan- Virtual local area networks (VLANs) are a wonderful wireless network security tool by enabling its separation technology. You can implement VLANs in several ways when working with your wireless LAN. VLANs allow you to. Separate different types of traffic based on the SSID to which they connect. however these appear to be channels rather than vlans, which is confusing
- Overlapping channels- Short Answer: Only use channel 1, 6, or 11. Longer Answer: In the United States, while channels 1-13 can be used for 2.4 GHz WiFi, only three channels are considered non-overlapping (channels 12 and 13 are allowed under low powered conditions, but for most cases are not used)
- signal strength- see RSSI
- ssid broadcast- The continuous transmission of packets from a Wi-Fi access point that announces its availability. Also called “beaconing,” if the network is secured with a password, users will see the SSID, but not be able to access it (see WEP and WPA).
- incorrect VLAN- Using the wrong wireless vlan, I understand what a vlan is but its confusing when incorporating wireless tech into it. Is this like a separate SSID or you some how are randomly assigned to a separate vlan when connecting to the SSID? I cant be perfectly sure on every thing so I’ll figure this out as we go.
So the overlapping channel thing kind of makes since you are only supposed to use 1, 6, or 11 but it still seems as if its miss labeled. Or maybe the vlan is the channel? Unclear but i’m sure ill understand it eventually so lets move on.
-
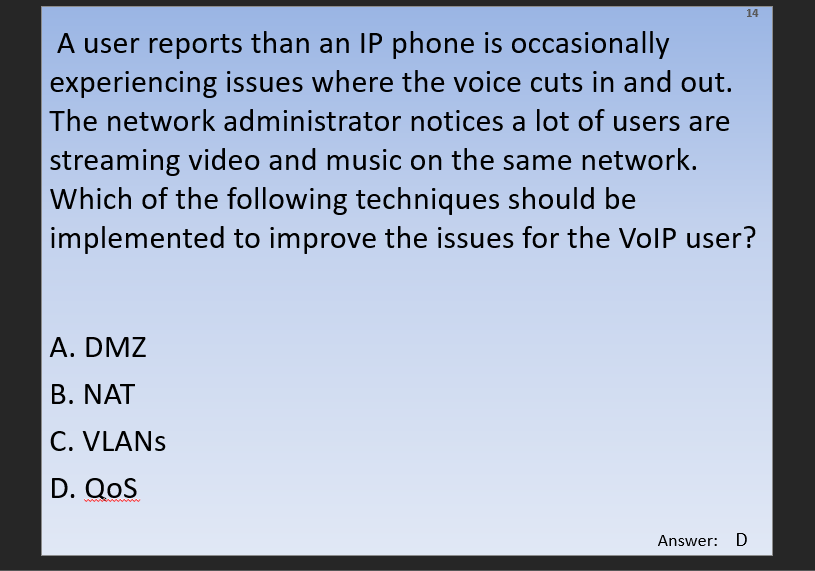
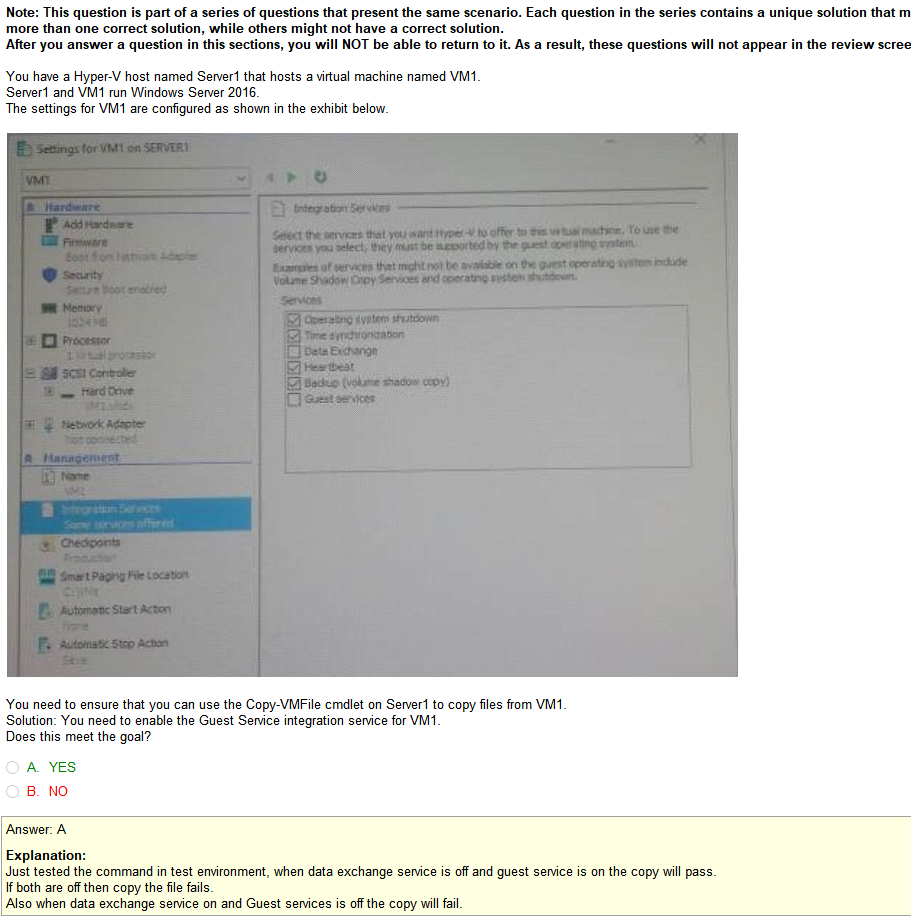
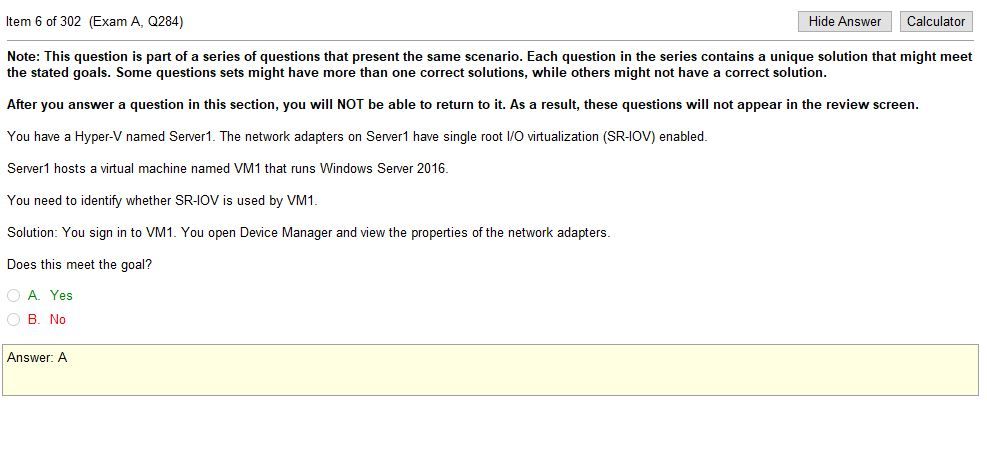
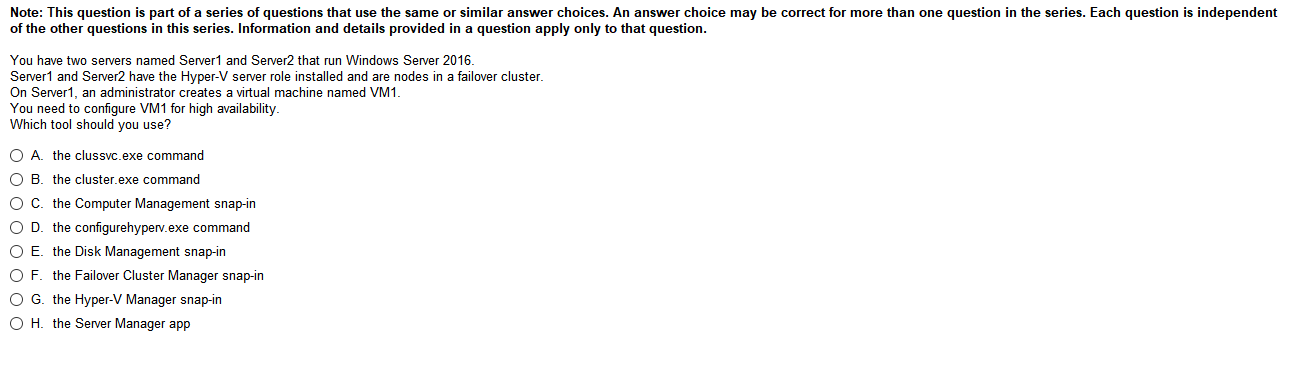
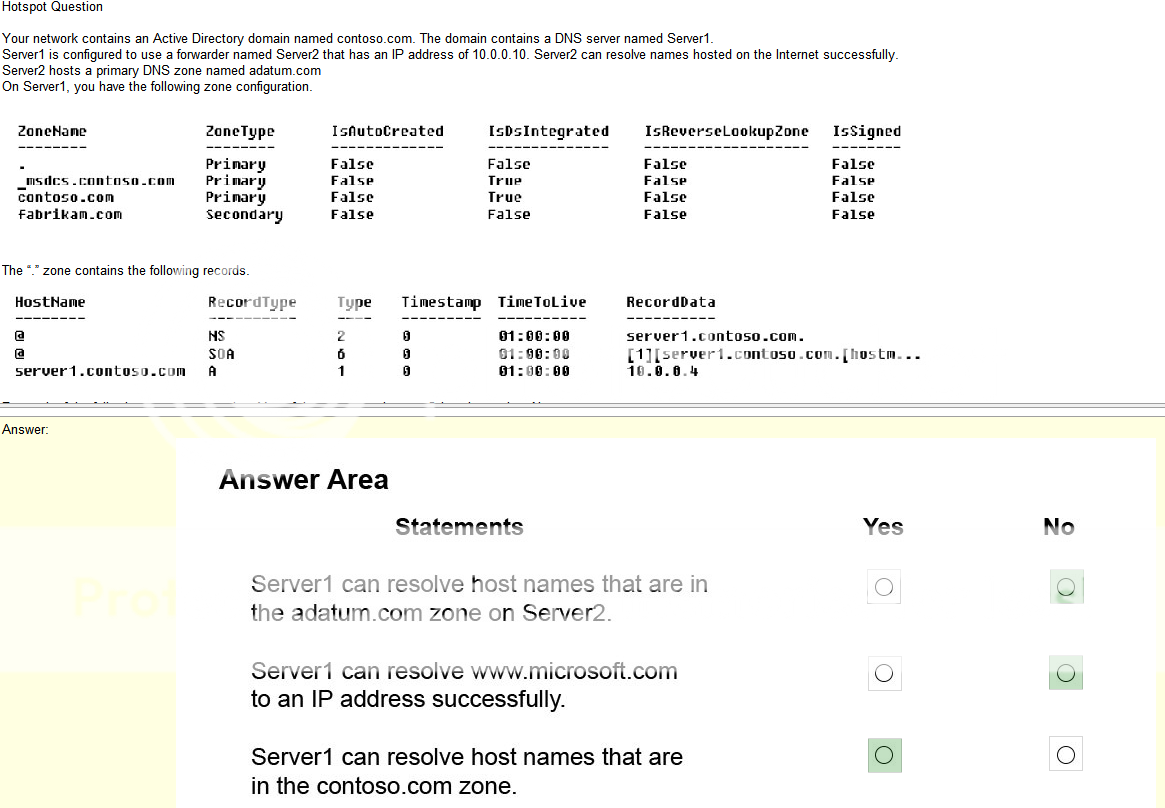
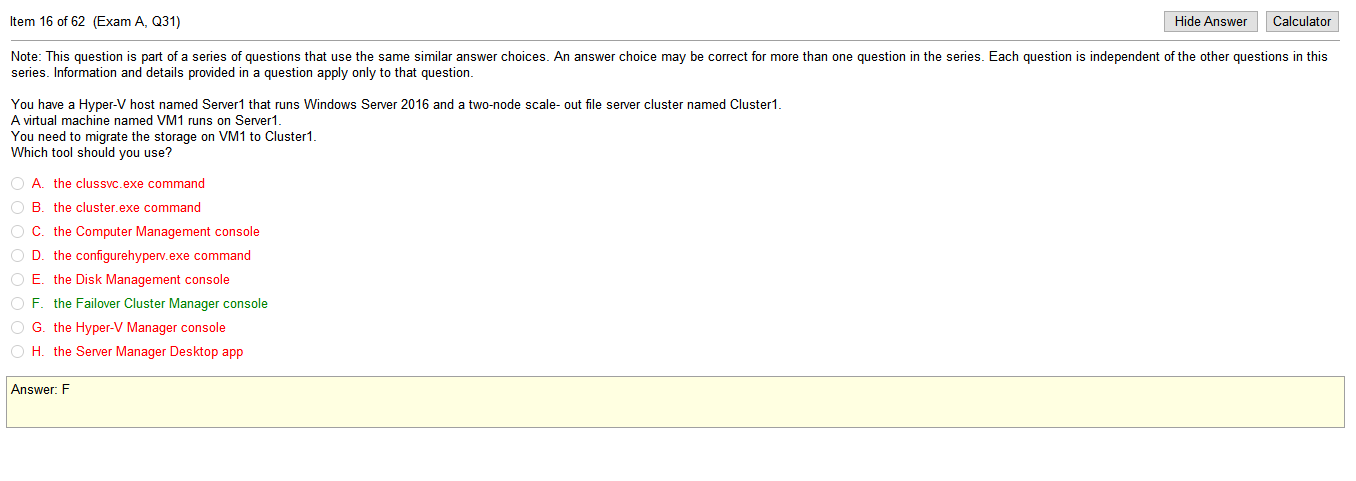
Answers
- DMZ- I feel like this is has been replaced by WAP or web application proxy in terms of naming conventions but its past the network firewall and less closed off to web traffic
- NAT- I’m assuming this is network address translation which could possibly have something to do with phones but I’m not sure
- VLAN- We just covered a VLAN but its a virtual network and I have no idea what it could have to do with phones but then again, I know absolutely nothing about VOIP tech to be honest
- QoS- QoS (Quality of Service) is a major issue in VOIP implementations. The issue is how to guarantee that packet traffic for a voice or other media connection will not be delayed or dropped due interference from other lower priority traffic. Ok google thats fairly broad but its clear that this is the issue in this case. ok.
-
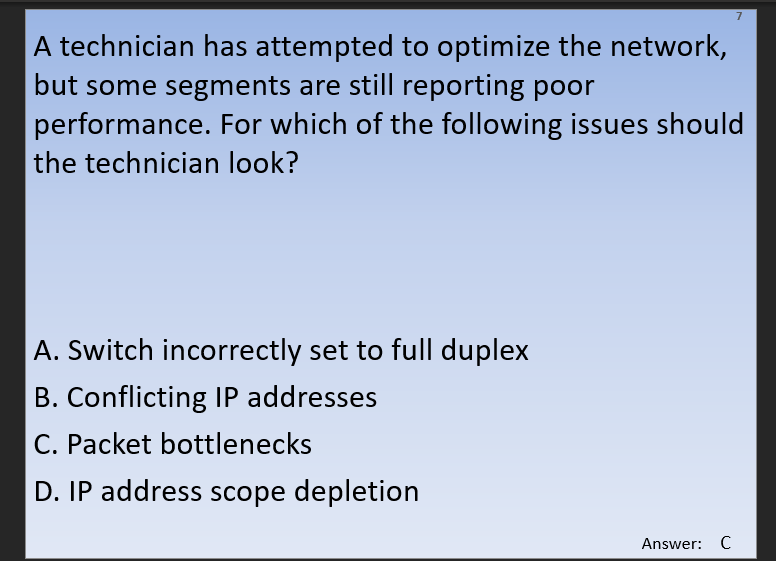
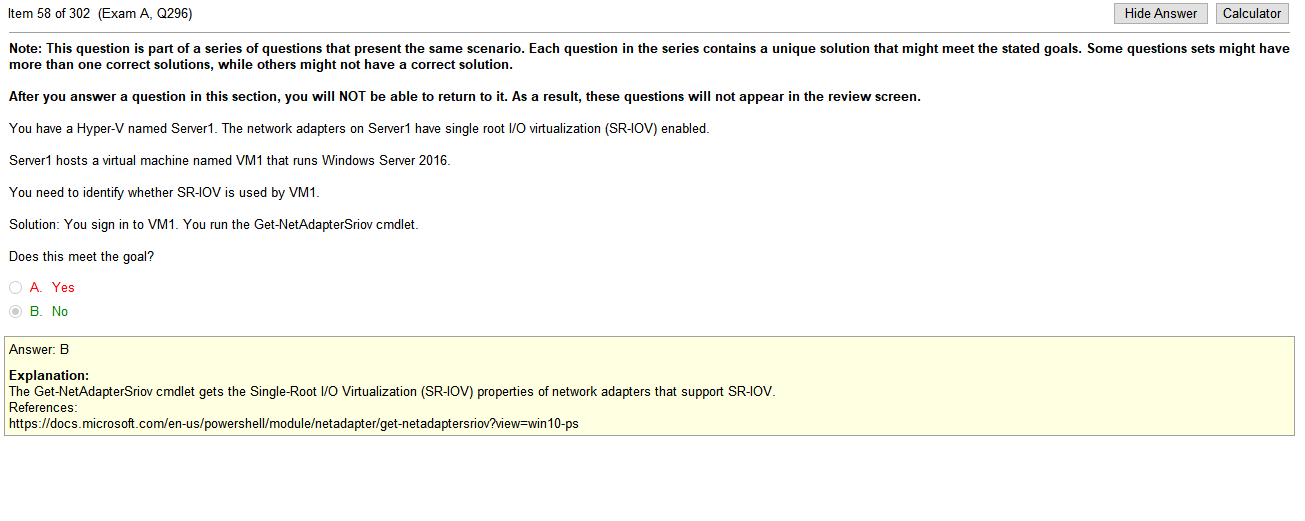
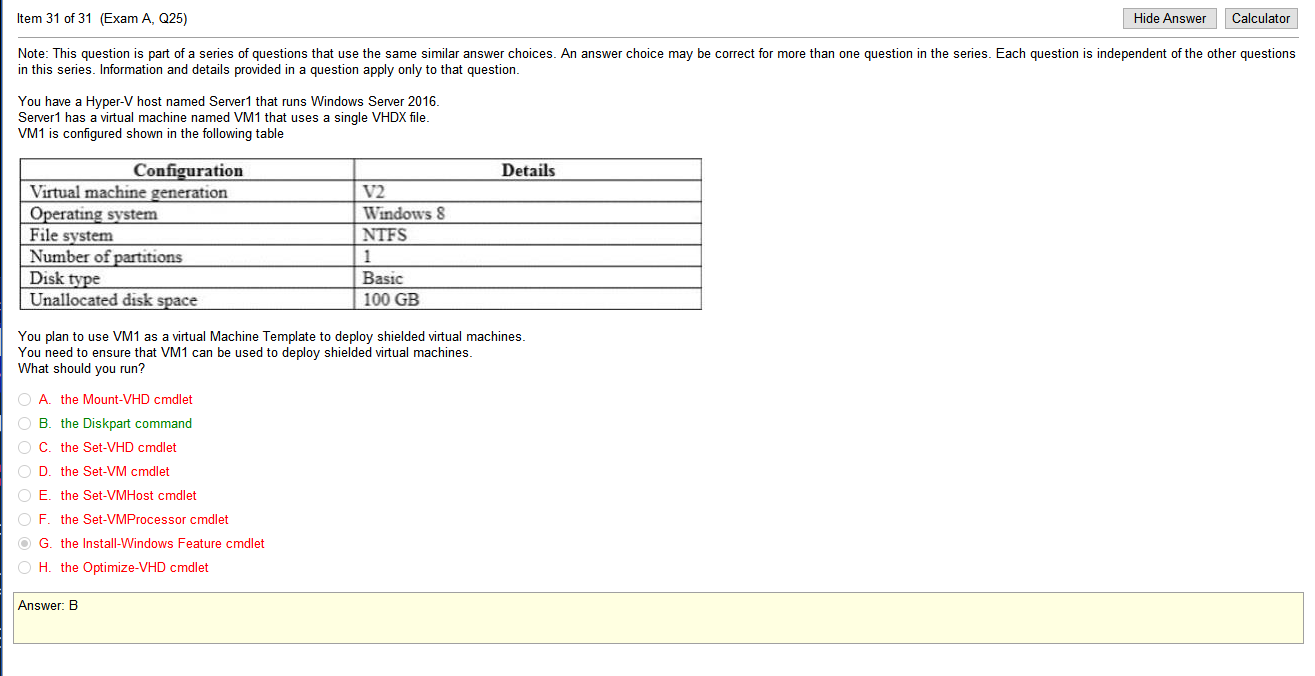
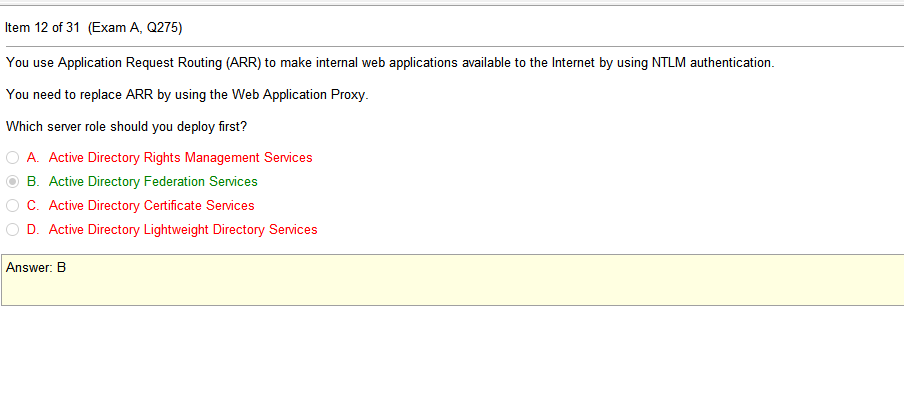
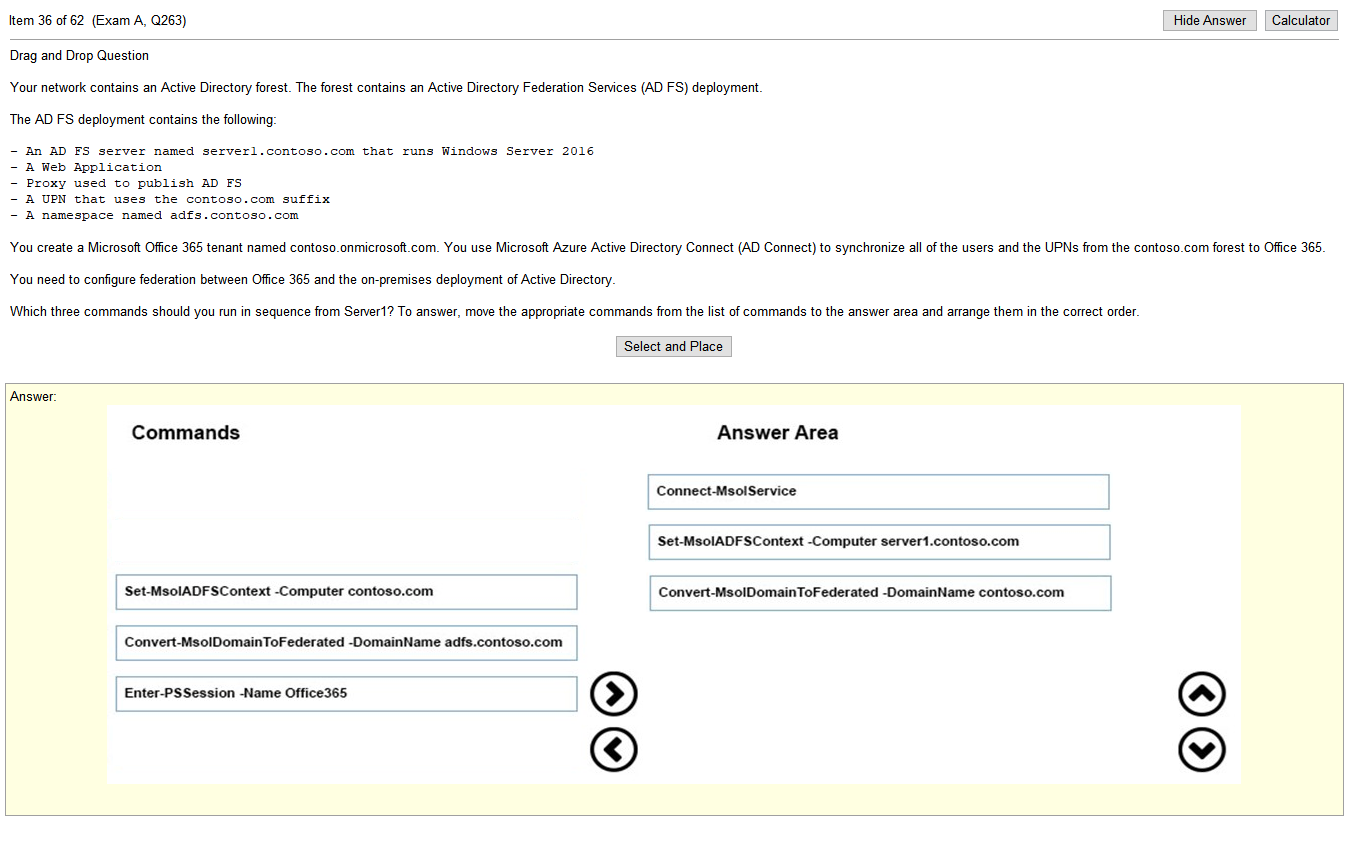
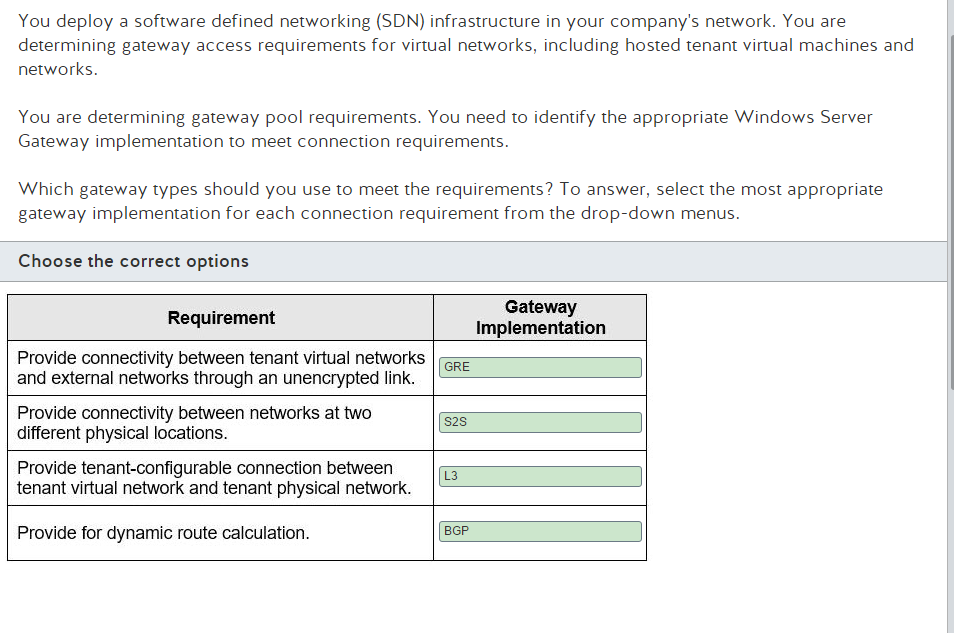
answers
- Switch set to full duplex- WiFi is Half Duplex – A wired Ethernet network is full duplex, meaning a device can send and receive, or upload and download, simultaneously. WiFi is half duplex, so if a client is sending data to the AP, the AP can not also send data to the same or any other client at the same time.
- Conflicting IP addresses- An IP address conflict occurs when two communication endpoints on a network are assigned the same IP address. Endpoints can be PCs, mobile devices, or any individual network adapter. IP conflicts between two endpoints normally render either one or both of them unusable for network operations
- Packet bottlenecks- A bottleneck occurs when bandwidth is unable to accommodate large amounts of system data at designated data transfer rate speeds. Road traffic is a common bottleneck analogy. For example, bottle necking is inevitable when only one of two busy road lanes is passable.
- IP address scope depletion- This is the DHCP server running out of addresses in a given address space causing clients to be unable to request an IP assignment for the network
I like this test, once you understand the definitions, so far, the answers are obvious. Clearly a performance issue would be the cause of a performance issue. I mean, given that I’m actually studying the right material. I may purchase a pretest from another location to verify that I’m actually studying the right material before dropping the money on the test.
Again, I don’t really know any of this because I don’t know squat about networking. I’m starting to realize it may be more than simply doing math. This excites me.
-
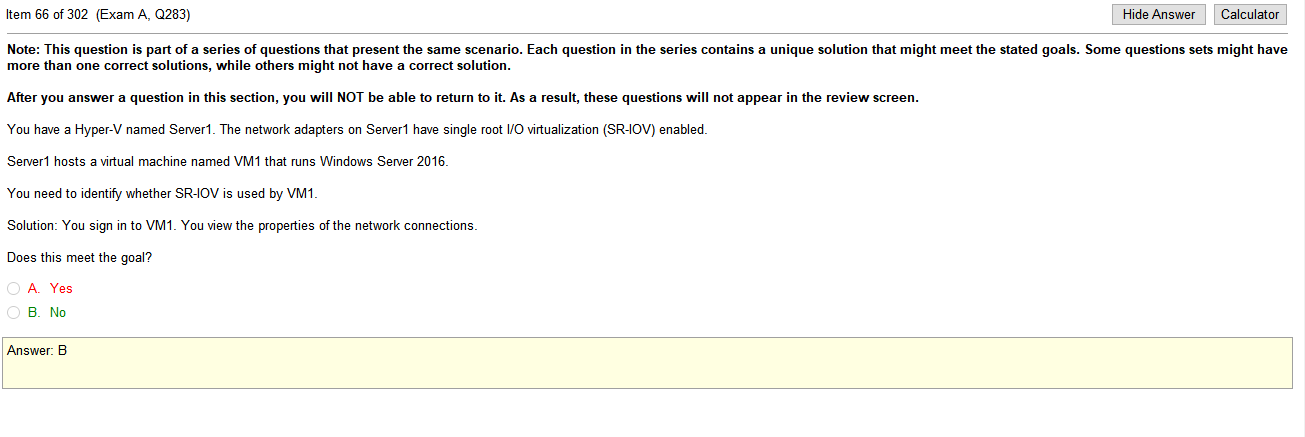
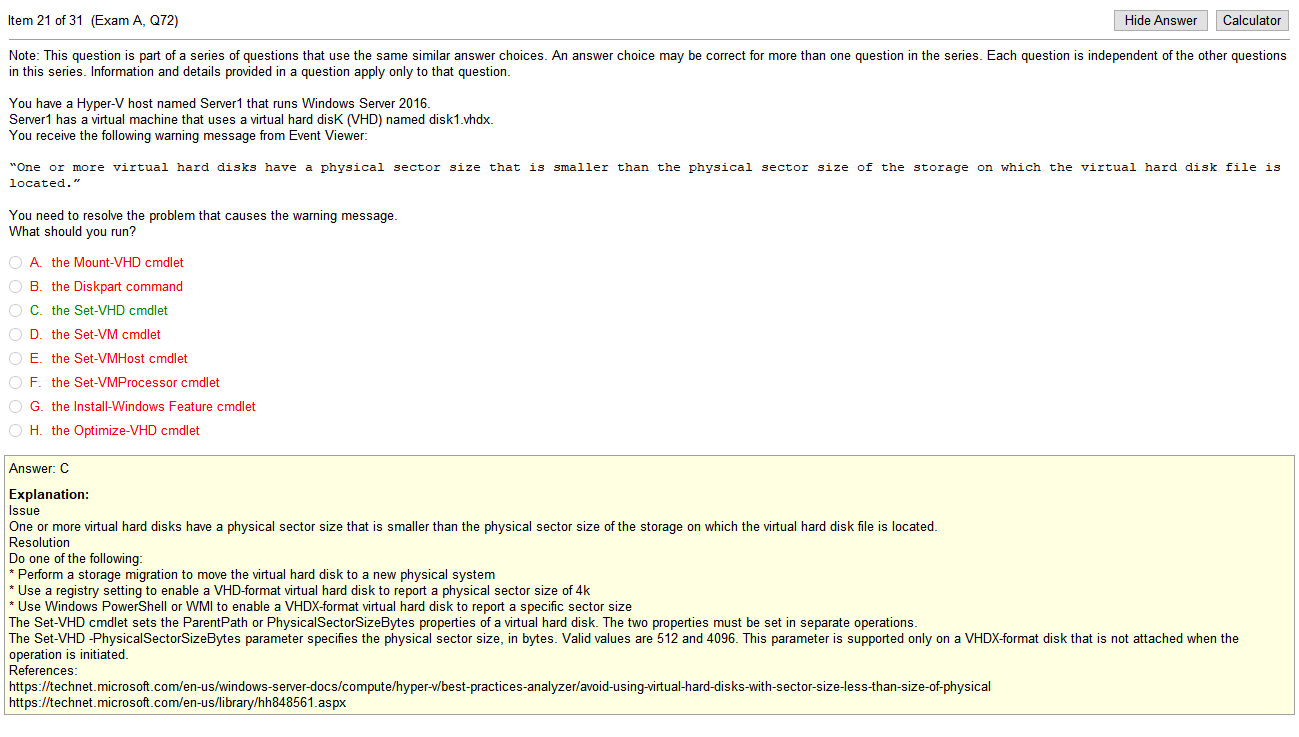
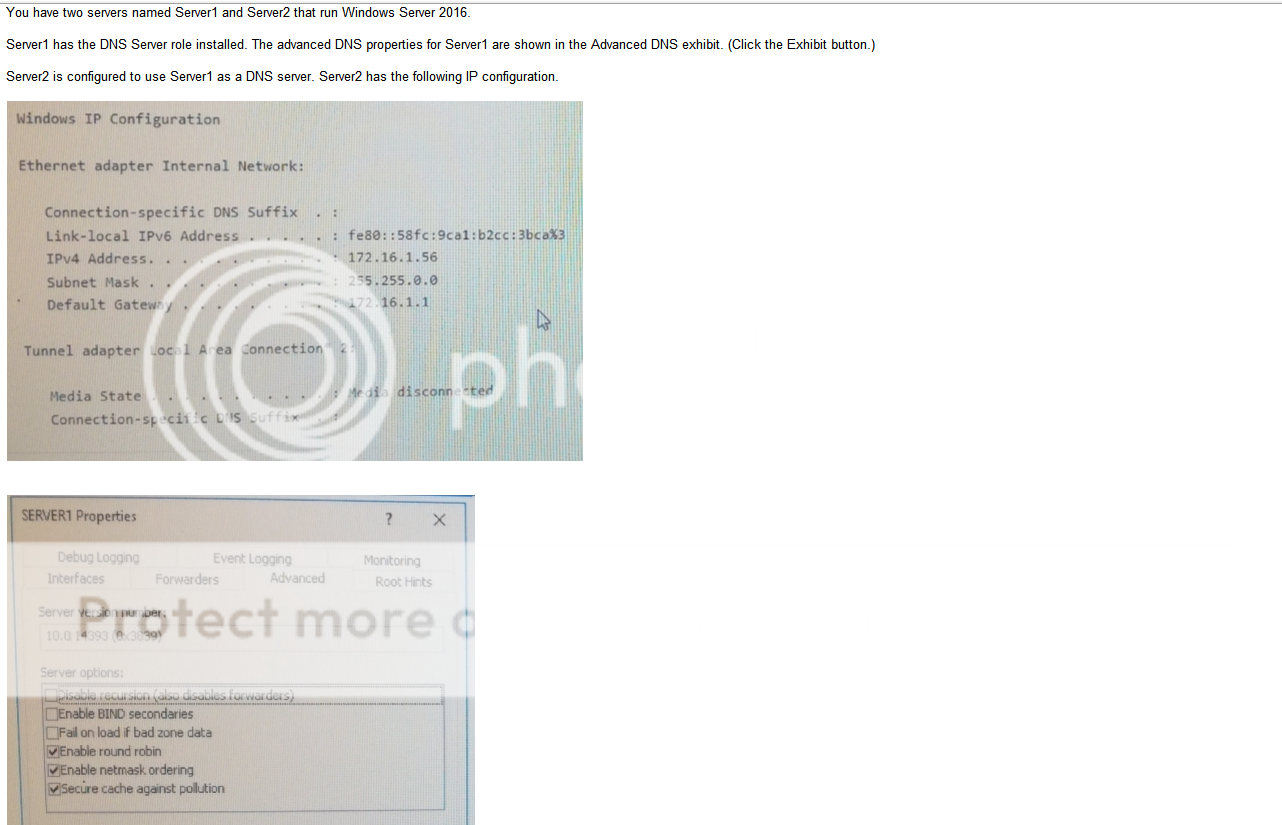
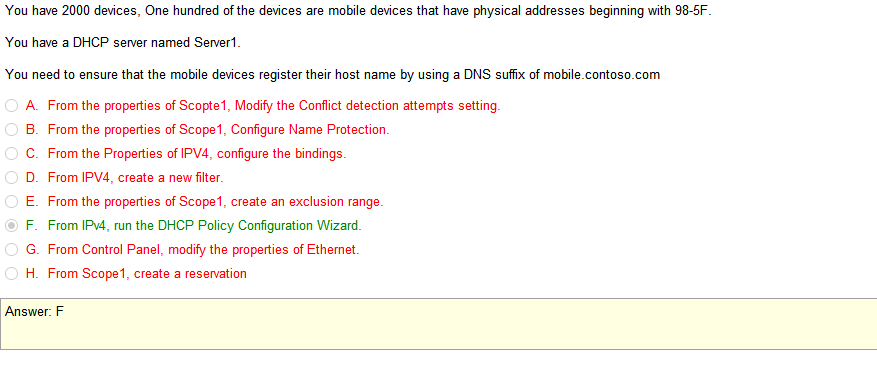
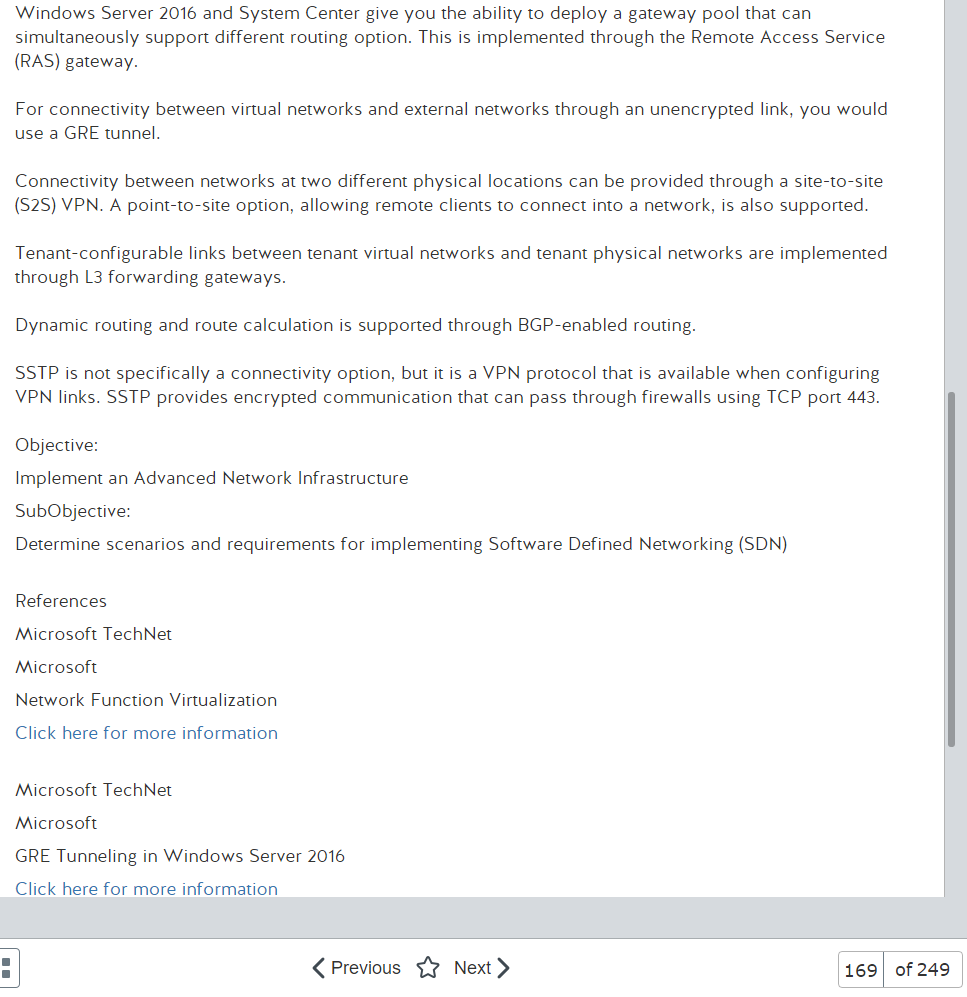
Answers
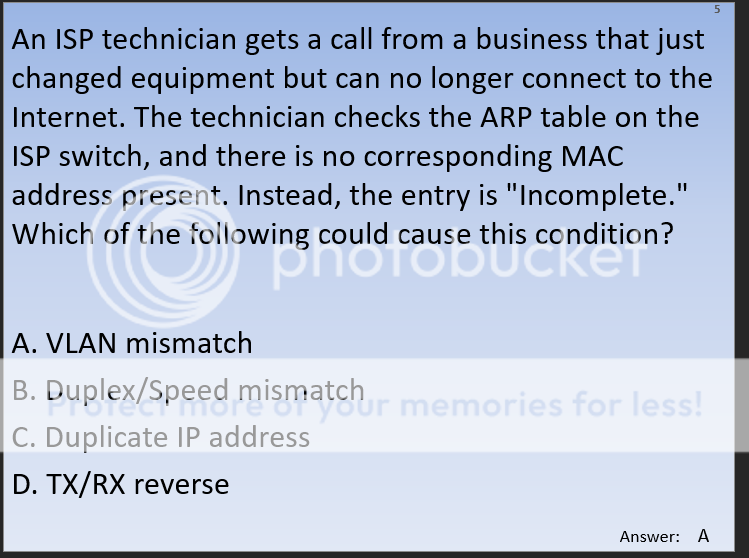
- VLAN mismatch- VLAN mismatch basically is saying that you have a device plugged into your Cisco device that has a different native VLAN than your switch. Clear as mud to me at this point
- Duplex/Speed mismatch-On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex. The effect of a duplex mismatch is a link that operates inefficiently. Duplex mismatch may be caused by manually setting two connected network interfaces at different duplex modes or by connecting a device that performs auto-negotiation to one that is manually set to a full duplex mode.
- Duplicate IP address- This will make both devices not functional, leasing issue
- TX/RX reverse- One particular type of cabling issue is the one in which the Transmit and the Receive pairs of a cable are inversed so the TX sides are connected to each other and the RX sides are connected to each other (as opposed to the correct way of connecting TX to RX).
So the answer still somewhat escapes me as I don’t understand the the exact issue described in the problem and there is an explanation on Cisco forums that provides all sorts of hot topics such as trunks and vlans and devices and I don’t know whats going on. I kind of get excited at that point to learn because I’m a nerd.
I guess that’s all for now but I really don’t know much of this so I’ll probably post a ton of stuff. I really hate that there isn’t one source for this stuff like TechNet but so far I can mostly make out the information on various websites/blogs