I took a little stay-cation break and have been preparing for a temp job this weekend. I have no idea what to do with money but Ill probably get some Wolverine TPB comics that
ive been trying to read for a while. I feel like my skill set as really improved as a result of this process. On twitter I shared that I got ~60% of the questions I got wrong on the last practice test right which hopefully I’ve committed a few more to memory which
would lead to a higher score going through all of the questions leading to my currently feared actual passing of the test. Its kind of weird I suppose to study for such a long period of time and become distracted in the waning days of study. However I may need to go
through the 411 to actually get a solid passing score on the actual 410 test. Im kind of hoping to go through the 411 and 412 pretest questions in this format as im sure they will be helpful in the future as I plan to continue on to server 16. The only way to ensure
success is constant study though a small break would be nice. However in my own personal worry I struggle with the idea that I may not pick back up with quite as much momentum so perhaps the best way is just not to take a break. Any way I feel that Network + should come in the breaks on server study as im kind of lacking in core network troubleshooting skills as its something that I have little to no hands on experience with. Obligatory personal paragraph out of the way lets get into it.
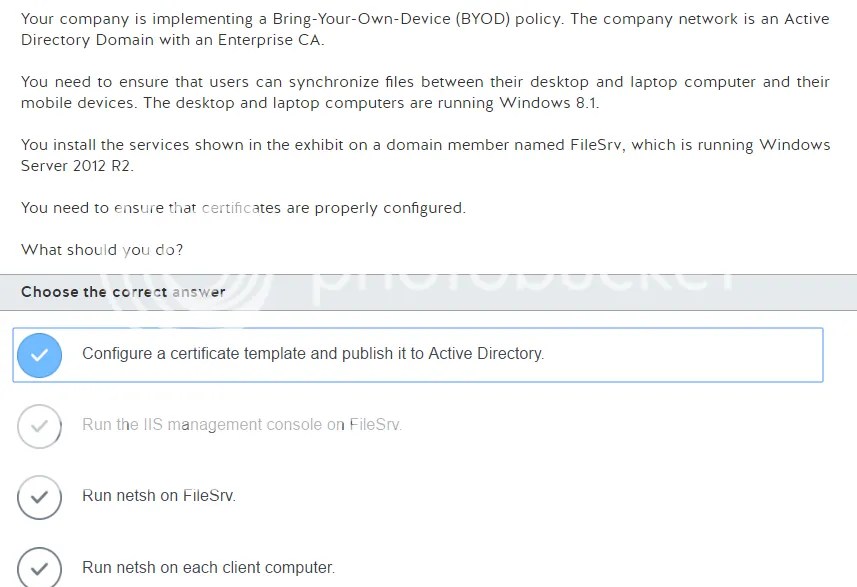
The most interesting note here is about the OU vs the domain group. Im not even exactly sure what they mean by “domain group” as it could be slightly more specific in the explanation. If you google “active directory domain group” no specific info comes up so I guess im unclear on exactly what they are talking about if its different from OU at this point in time.
After reading the answer it seems clear that deleting the DNS cache file on a server is a bad idea. Im curious about this though doesthis delete the whole zone or what exactly would that do?
Google isnt exactly clear on this point either. More research for a later date but it is an interesting topic. These are such helpful study resources and I feel like an experienced admin would know these things but someone studying to be an admin is clueless. I think
the point they are trying to make with this can be found in TechNet
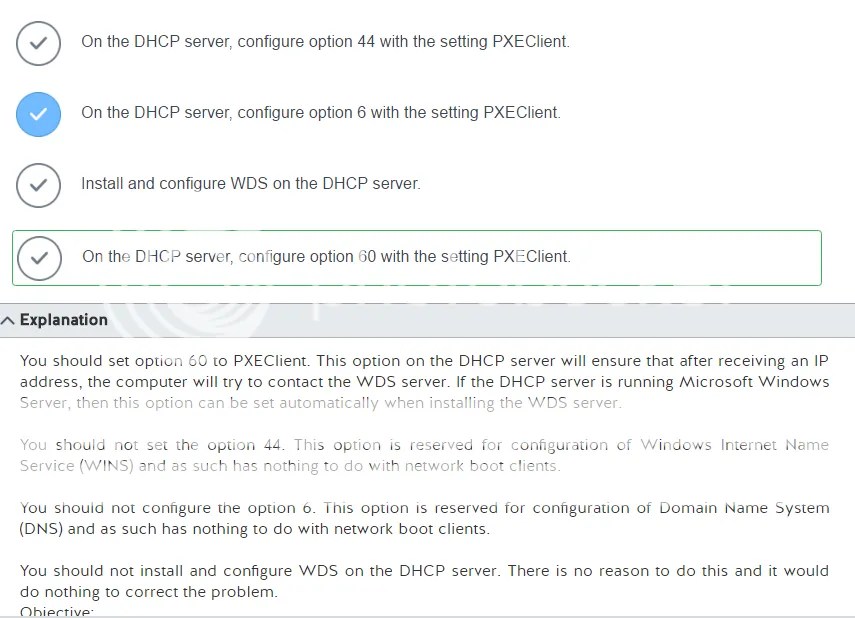
I really like this question however I really wish that It was more specific in exactly where this configuration was taking place. So I configure the address of DNS in the DHCP server. Understood, no idea where though.
I did find a youtube video and if you pay real close attention around 2 minutes you can see a DNS tab, assuming that’s what’s going on.
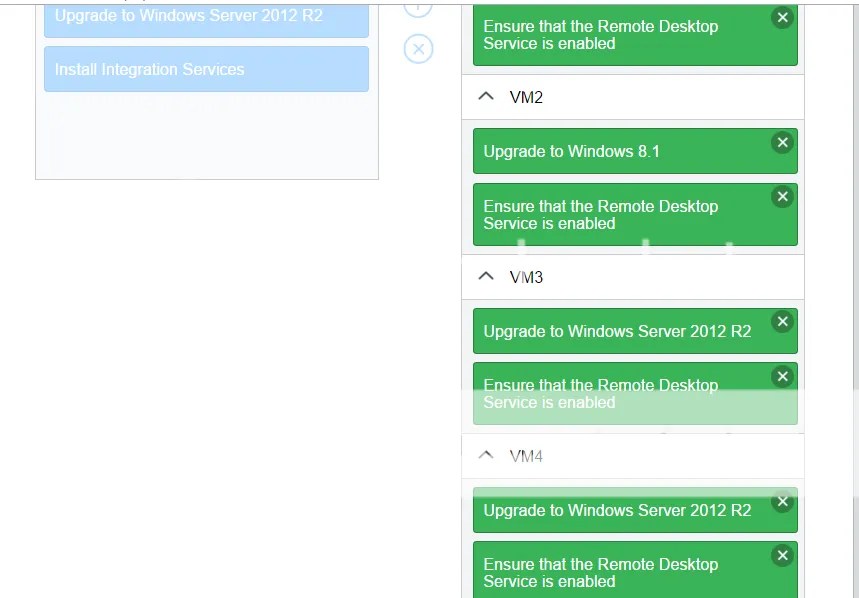
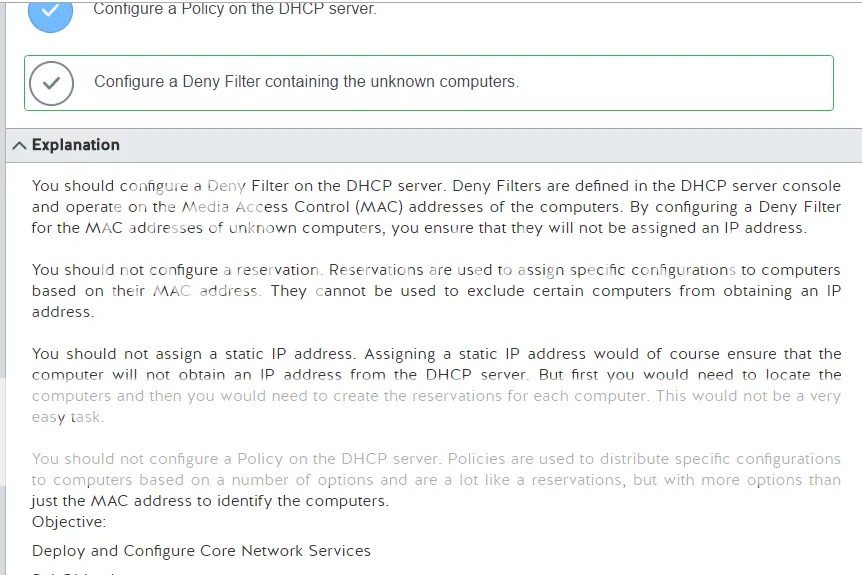
This question comes up a whole lot so im glad they did a version of this question that was so plain.
The longer string converts to server core, the shorter one still leaves a few gui tools and desktop experience is not installed by default.
I realize Im one question shy of 5 but I’ve got 4 more set to blog from this round of questioning so im going to split them in half as opposed to doing a longer 8 question post.